1.2 Million+ Downloads
Runtime Security Enforcement
KubeArmor (CNCF Sandbox open-source project) is cloud native runtime security enforcement engine. It helps with workload hardening and sandboxing by leveraging eBPF and Linux Security Modules, preemptively mitigating any potential security attacks.

KubeArmor DataSheet
Download PDFModelArmor DataSheet
Download PDFARCHITECTURE
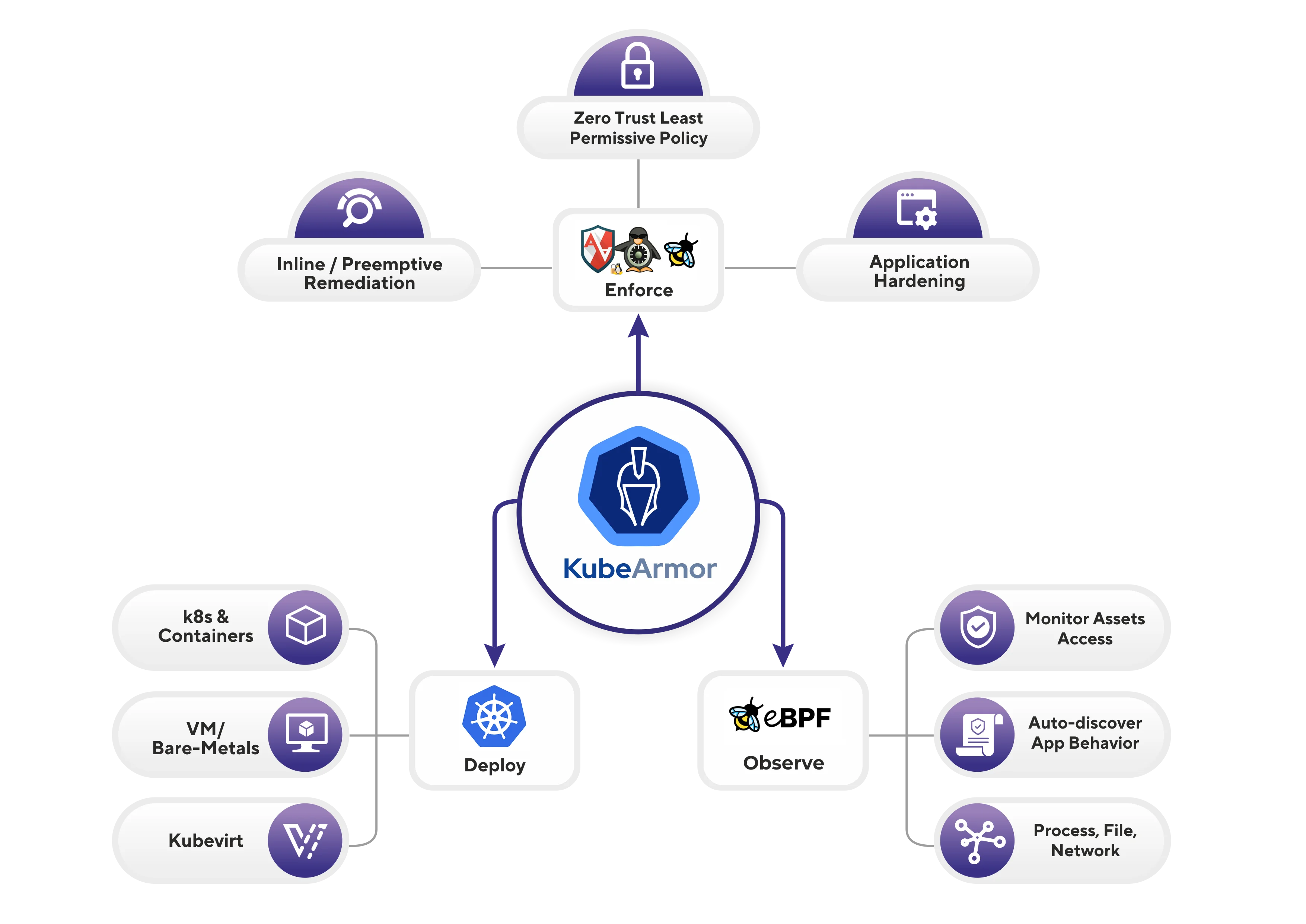
First K8s Security Engine to Leverage BPF-LSM
KubeArmor is a runtime Kubernetes security engine. It uses eBPF and Linux Security Modules(LSM) for fortifying workloads based on Cloud Containers, IoT/Edge, and 5G networks. It enforces policy-based controls.
USE CASES
What Makes KubeArmor Unique?
Inline Mitigation
KubeArmor lessens the attack surface on pods, containers, and virtual machines. For inline mitigation, it uses Linux Security Modules (LSMs) like AppArmor, BPF-LSM, and SELinux to provide security without changing the pod or container or without host-level adjustments.
Simplicity with LSMs
KubeArmor simplifies their intricacies and makes enforcing policy simple. It functions as a non-privileged daemonset and has host, pod, and container monitoring capabilities.
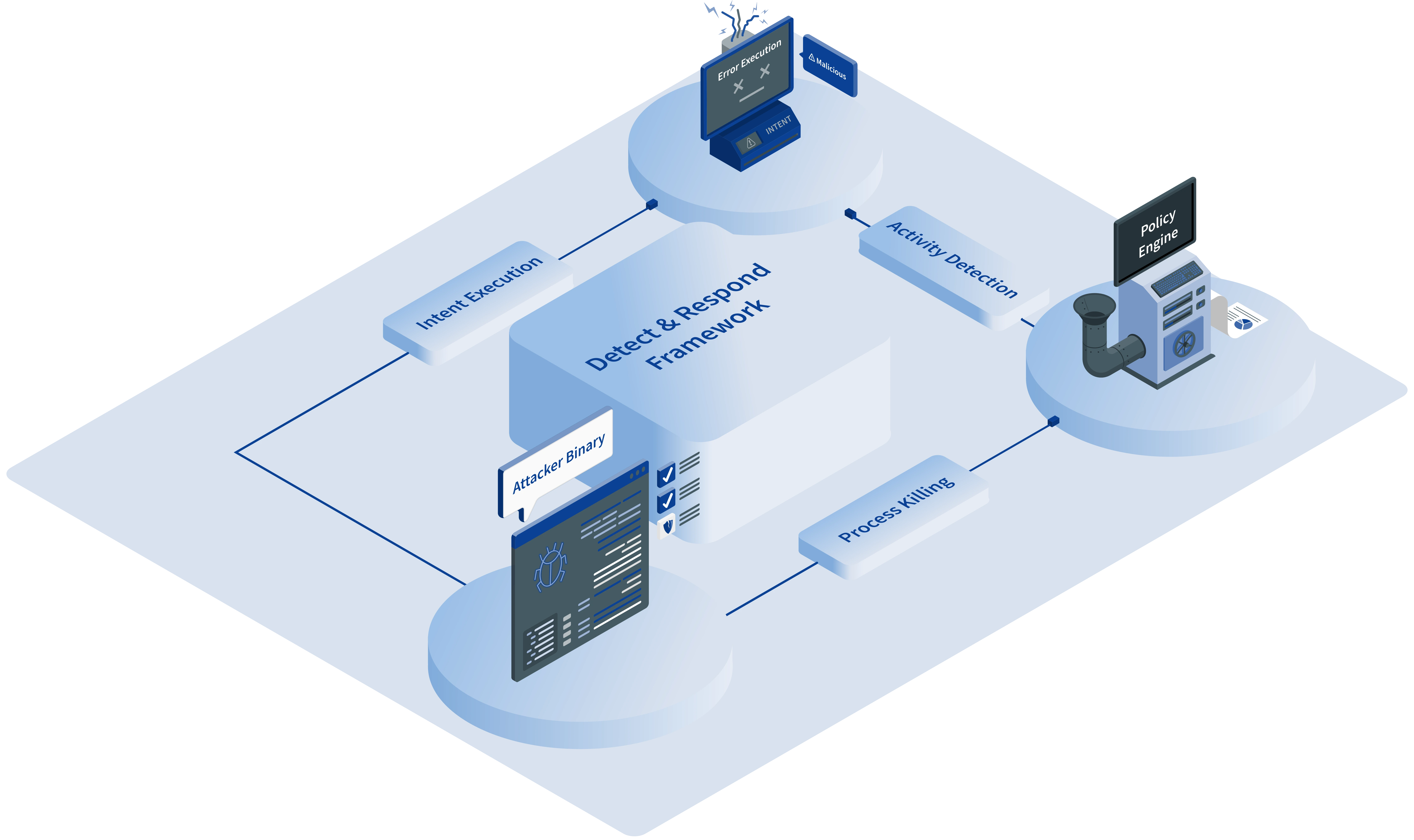
Flaws of Post-Attack Mitigation
Our inline approach is proactive, in contrast to post-attack mitigation, which kills processes after malicious intent is observed. Attackers are able to run code and possibly elude detection with the help of post-attack mitigation.
Challenges of Pod Security Context
K8s native Pod Security Context has limitations, including difficulties in predicting available LSMs and a lack of support for BPF-LSM.
Multi-Cloud Challenges
Dealing with pod security contexts is difficult since cloud providers use various default LSMs.
INSTALLATION
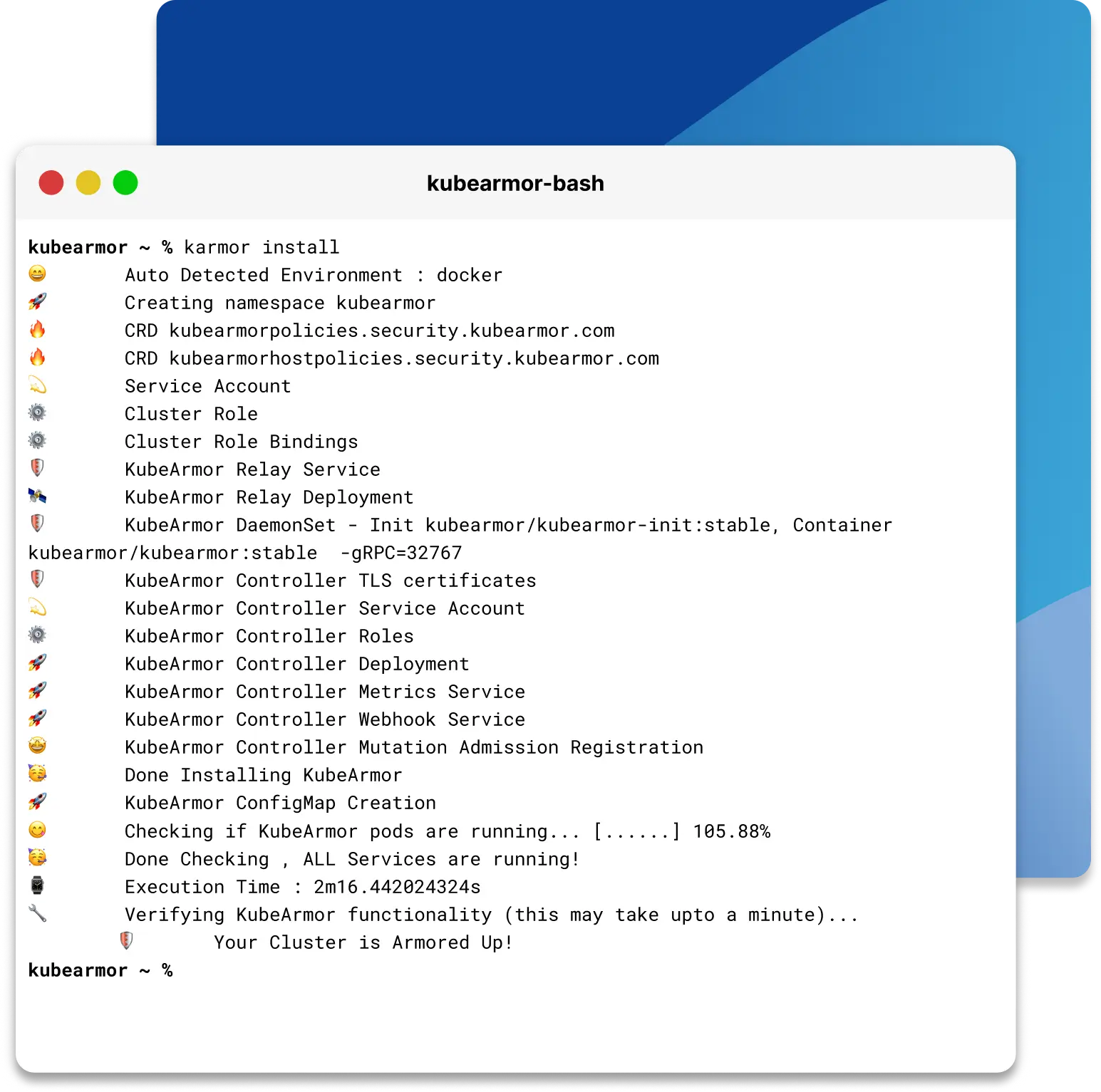
How to Install KubeArmor?
Boost your security with KubeArmor in simple steps
Download and install KubeArmor via helm chart
helm repo add kubearmor https://kubearmor.github.io/charts
helm repo update kubearmor
helm upgrade --install kubearmor-operator kubearmor/kubearmor-operator -n kubearmor --create-namespace
kubectl apply -f https://raw.githubusercontent.com/kubearmor/KubeArmor/main/pkg/KubeArmorOperator/config/samples/sample-config.yml
For configuration options and further information
Read DocumentationFEATURES
Monitor and Enforce Policies To Prevent Sophisticated Attacks
Behavior Restriction
Within workloads, KubeArmor limits particular behaviors of processes, file access, networking operations, and resource usage.
Runtime Policy Enforcement
Based on container or workload identities, LSMs are used to enforce security policies in real-time.
Kubernetes-Native
Policy development based on Kubernetes metadata. This allows for enhanced Kubernetes-native security enforcement.
Policy Violation Logging
Get logs for policy breaches while keeping track of container processes via eBPF.
Simplified Policy Descriptions
KubeArmor manages LSM complexity to simplify policy descriptions.
Network security
KubeArmor regulates communications between containers using network system calls.
Kernel Support Matrix
VERSION CHANGELOG
Exciting Updates and Announcements
EXPANSIONS
What's new?
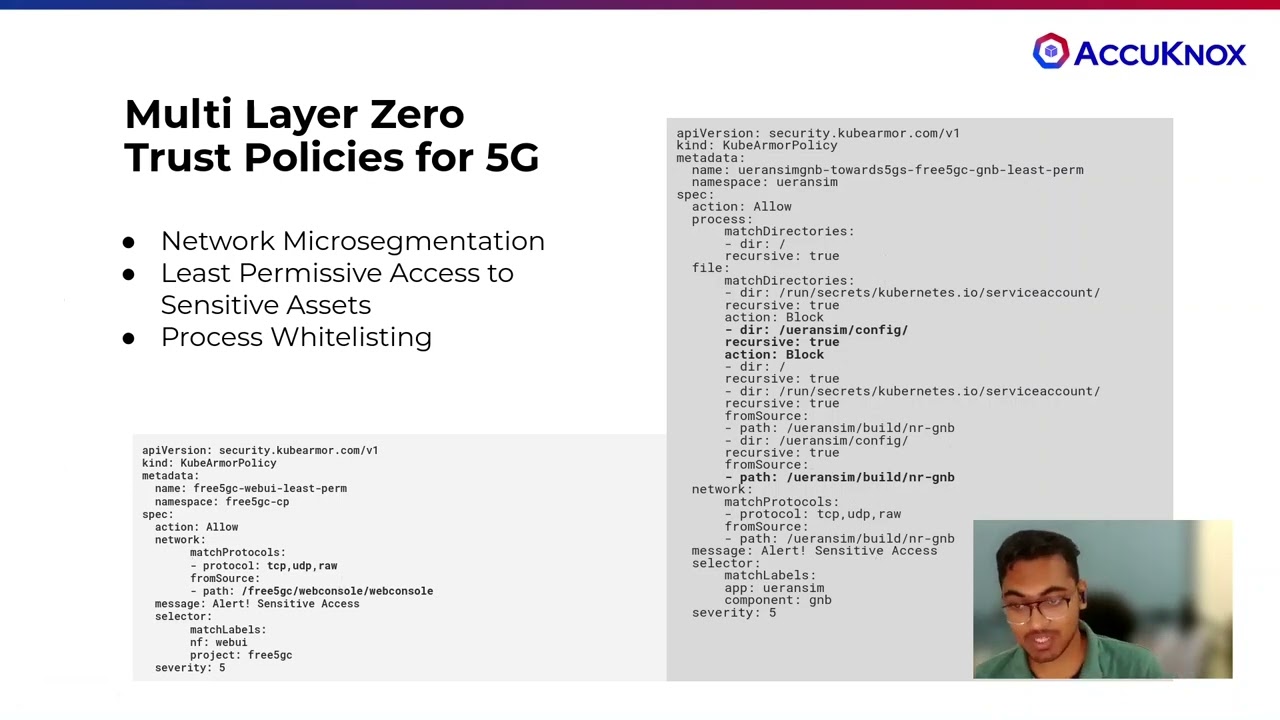
IoT/Edge Security
KubeArmor provides the ability to restrict specific behavior of process executions, file accesses, networking operations, and resource utilization inside of your workload level.
5G Control Plane Security
KubeArmor directly enforces security policies using Linux Security Modules (LSMs) for each workload based on the identities (e.g., labels) of given containers or workloads.
BLOGS
Open Source Solutions for Kubernetes Security
FIRESIDE CHAT
Securing Kubernetes Clusters Effectively
TESTIMONIALS
Developers Love Using KubeArmor

Kubesploit
KubeArmor is a cloud-native runtime security enforcement system that restricts the behaviour (such as process execution, file access, and networking operations) of pods, containers, and nodes (VMs) at the system level

Oracle Developers
We're excited to announce that #developers can now use @KubeArmor, a runtime security engine that can enhance security of containerized applications on Oracle Container Engine for #Kubernetes. https://social.ora.cl/60153sOwv

Whitney Lee
♫~ On tomorrow's Enlightning, @daemon1024 will teach @KubeArmor, a @CloudNativeFdn project that protects your modern, cloud native workloads at runtime!

Sachin Maurya
Finally, I Graduated from the @linuxfoundation Mentorship Program. It was fun and lots of learning working on the @KubeArmor Project. I learned a lot about Container Security and #eBPF. Now I'm looking to continue working on this awesome technology.

ITNEXT DevOps
Protecting Your Kubernetes Environment With KubeArmor by Patrick Kalkman at #ITNEXT. #containers #cybersecurity #kubernetes #cyberattack #hacker https://itnext.io/protecting-your-kubernetes-environment-with-kubearmor-76b02fc2209b?source=rss----5b301f10ddcd---4… (s)

Manish Kapur
Happy to share that @KubeArmor Zero trust #Security solution for #Kubernetes has added support for Oracle Kubernetes Engine and @OracleLinux. Thank you to our friends at @AccuKnox https://github.com/kubearmor/KubeArmor/wiki/KubeArmor-support-for-Oracle-Container-Engine-for-Kubernetes-(OKE)… #k8s #cncf
Adopted By
Milestones
2020
- KubeArmor project architecture
- MVP Launch
2021
- CNCF Sandbox Acceptance (November 16)
- Dec 17, Released v0.1 - stable version
2022
- Surpassed 300K+ downloads
- Gained traction in the open-source community
- Host Policy Enforcement support
2023
- Reached 10+ industry adopters, validating enterprise-grade capabilities
- Listed on AWS and Redhat Marketplace
- Released v1.0 - production-ready solution
2025
- Over 1+ Million downloads
- Earned 1,300+ GitHub stars, showcasing community engagement
- Listed on Oracle and Digital Ocean Marketplace
- Launched comprehensive KubeArmor Book, enhancing user education
- Introduced the KOSHER program
COMMUNITY
Join Our Awesome Community
We are a CNCF Sandbox project.
The Linux Foundation® (TLF) has registered trademarks and uses trademarks. For a list of TLF trademarks, see Trademark Usage.
Effortless and Efficient Runtime Security in Minutes
KubeArmor supports public and private Kubernetes deployments